Want to use OKTA Authentication in Oracle APEX applications? Read a handy step-by-step guide that’ll take you through the setup process.
This blog post will help you set up OKTA Authentication with APEX and then deliver the users’ OKTA Groups to APEX and map them to custom roles. It extends another article of mine to enable OKTA Authentication.
Instructions
1. Sign up for an OKTA Account (it isn’t free, but there’s a time-limited trial)
2. Save the Login & Org URL shown on the “Welcome” page in a Notepad file
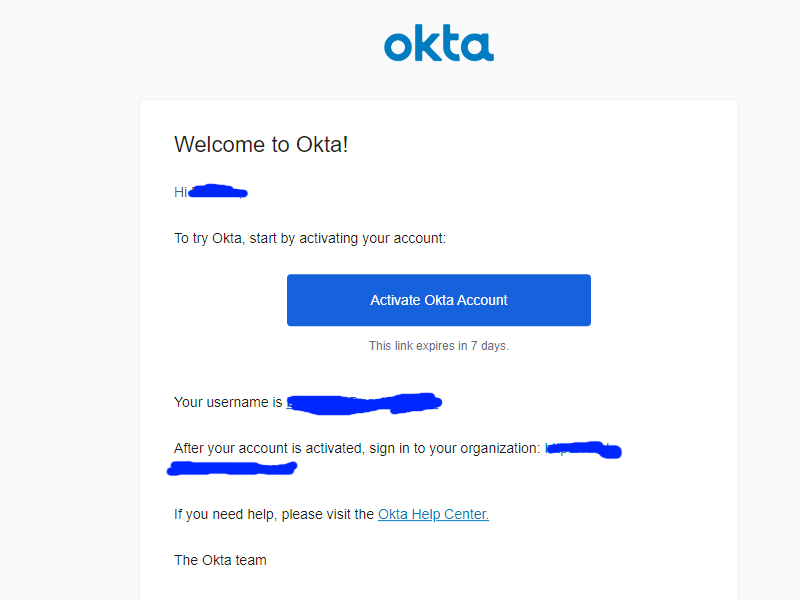
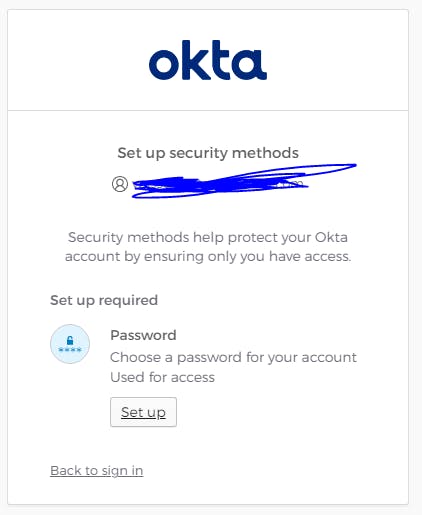
3. Wait for the confirmation email and Activate the account by setting a new password. Elect to set up the MFA later
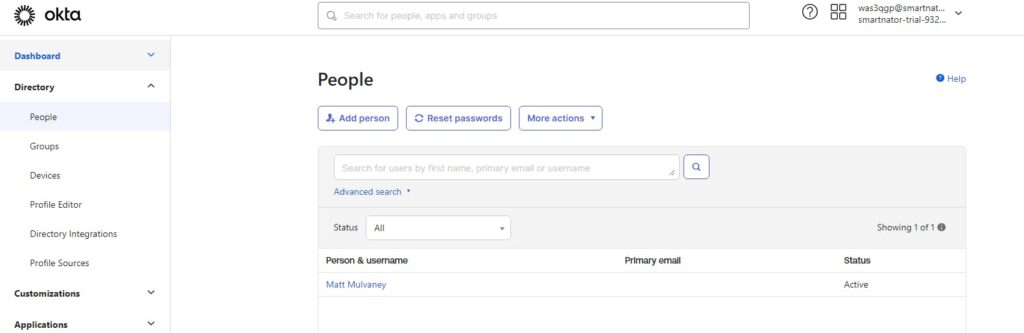
4. Click Directory > People and view the users. Optionally, you can also add new people
5. Click Directory > Groups > Add Group > Name = APEX > Save
6. Click Directory > Groups > Add Group > Name = Supervisors > Save
7. Click Directory > Groups > Add Group > Name = Empty > Save
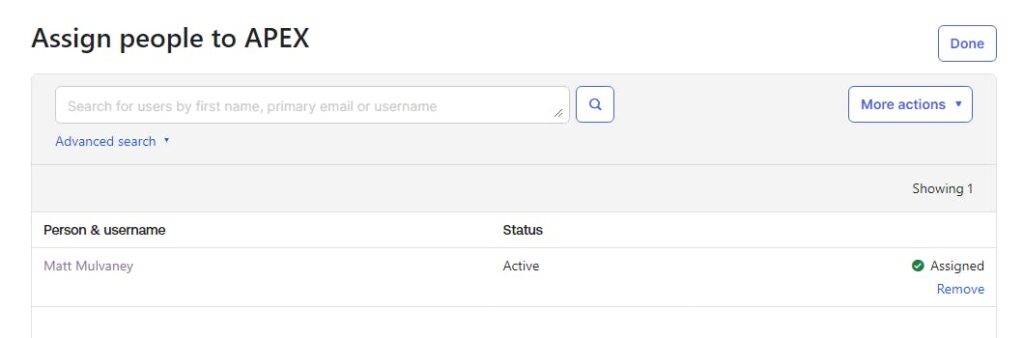
8. Click on group APEX > Assign People > + (the plus symbol next to your username) > Done
9. Follow the Database & APEX Configuration steps in my Achieving a SaaS Model for multi-tenant APEX Applications using Oracle IAM Domains article
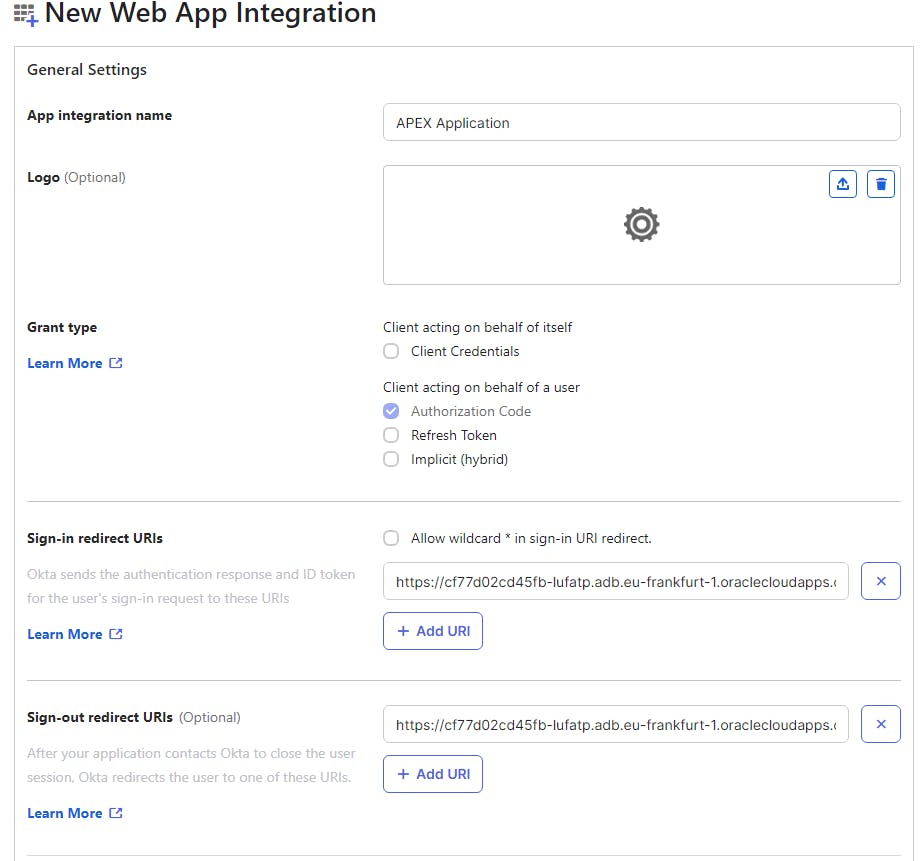
10. Click Applications > Applications > Create App Integration
11. Select OIDC – OpenID Connect & Web Application and click Next
12. Use the following setting in OKTA
App Integration Name = APEX Application
13. Run the following in your SQL Workshop
select APEX_AUTHENTICATION.GET_CALLBACK_URL from dual;
When you get the results, copy everything up to the callback phrase, for example:
https://apex.oracle.com/pls/apex/apex_authentication.callback
Paste this into Sign In Redirect URLs in OKTA.
14. In the Post-logout redirect URL type in the following (we will use DOMAIN3 in this example here)
[BASE URL]f?p=[APPLICATION ALIAS]:1::APEX_AUTHENTICATION=DOMAIN3
For example:
https://apex.oracle.com/pls/apex/f?p=T-PRODUCTS:1::APEX_AUTHENTICATION=DOMAIN3
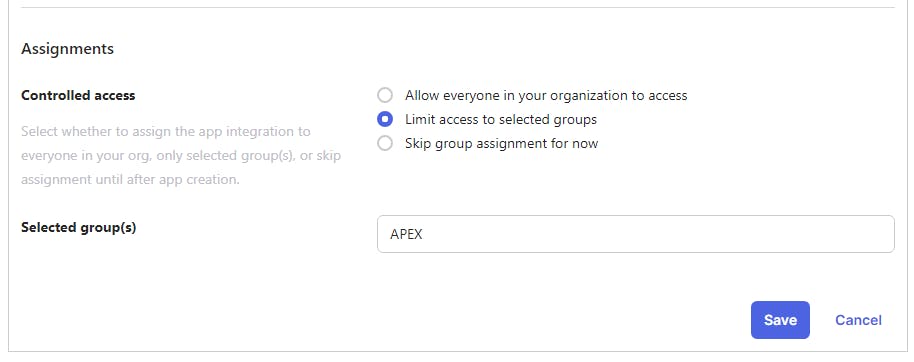
15. For Controlled access, select Limit access to selected groups and choose the group APEX
16. Leave all settings as they are. If it resembles what you see in the following screenshot, click Save
17. Copy the Client ID & Secret and paste it to a Notepad file
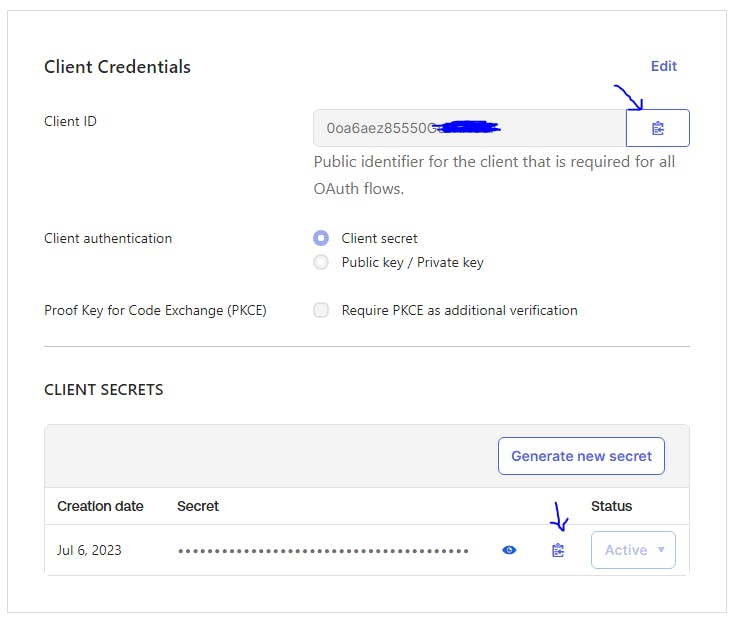 18. Optional – for demonstration purposes, we’ll switch to Password only, deactivating MFA
18. Optional – for demonstration purposes, we’ll switch to Password only, deactivating MFA
- In OKTA click Security > Authentication Policies > Password Only ~ View > Add App > APEX Application > Add >; Close
- Click Switch Policy > Switch Policy > Save
19. Next, we need to set up an API key
Click Security > API > Token > Create Token > mytoken > Create Token > copy value to a Notepad file > Ok Got It
20. Next, set some Privileges
Click Applications > Applications > APEX Application > OKTA API Sscopes > okta.groups.read > ✔️Grant
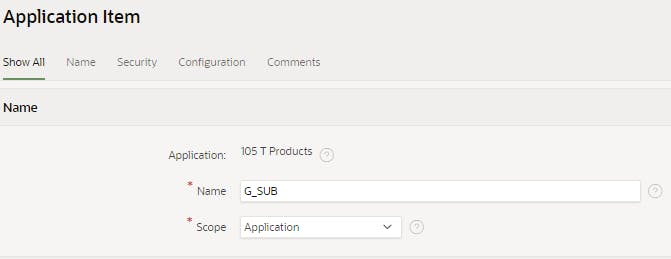
21. In APEX > Application Builder > Shared Components > Create > Name = G_SUB > Create Application Item
22. In APEX, click App Builder > Workspace Utilities > Web Credentials > Create
Use the following table:
| Name | Value |
| Name | OKTA.APEX.DOMAIN_3 |
| Client ID or Username | Paste in from Notepad |
| Client Secret or Password | Paste in from Notepad |
| Verify Client Secret or Password | Paste in from Notepad |
23. Click Create
24. Click APEX Application > Authentication Schemes > Create
25. Click Next on Based on a pre-configured scheme from the gallery
Use the following table
| Name | Value |
| Name | DOMAIN3 |
| Scheme Type | Social Sign-In |
| Credential Store | IAM.APEX.DOMAIN_3 |
| Discovery URL | https://${yourOktaOrg}/.well-known/openid-configuration, where ${yourOktaOrg} is replaced with your OKTA URL, like https://dev-999999-admin.okta.com/.well-known/openid-configuration see https://developer.okta.com/docs/concepts/auth-servers/#org-authorization-server-discovery-endpoints for more details) |
| Scope | profile |
| Username | name |
| Additional User Attributes | sub,profile |
| Map Additional User Attributes To | G_SUB |
26. Click Create Authentication Scheme
27. Click on Authentication Scheme DOMAIN3
Use the following table
| Name | Value |
| Source | Paste in Code Below |
| Post-Authentication Procedure Name | p_post_processing |
| Switch in Session | Enabled |
| Post-Logout URL | URL |
| URL | Your Post-logout redirect URL e.g apex.oracle.com/pls/apex/f?p=T-PRODUCTS:1::.. |
PROCEDURE p_post_processing
IS
l_clob CLOB;
j APEX_JSON.t_values;
l_group_names apex_t_varchar2;
l_api_key_c CONSTANT VARCHAR2(256) DEFAULT '<YOUR API KEY>';
l_org_url_c CONSTANT VARCHAR2(256) DEFAULT 'https://<YOUR ORG URL>.okta.com';
BEGIN
apx_tenant.p_set_tenant_id( 'DOMAIN_3');
apex_web_service.set_request_headers(
p_name_01 => 'Content-Type',
p_value_01 => 'application/json',
p_name_02 => 'Accept',
p_value_02 => 'application/json',
p_name_03 => 'Authorization',
p_value_03 => 'SSWS ' || l_api_key_c
);
l_clob := apex_web_service.make_rest_request(
p_url => l_org_url_c || '/api/v1/users/' || :G_SUB || '/groups',
p_http_method => 'GET');
APEX_JSON.PARSE(p_values => j, p_source => l_clob);
FOR i IN 1 .. APEX_JSON.GET_COUNT(p_path=> '.', p_values=> j)
LOOP
-- add all group names to l_group_names
apex_string.push (
p_table => l_group_names,
p_value => apex_json.get_varchar2(p_path=>'[%d].profile.name',p0=> i,p_values=>j));
END LOOP;
-- save group names in session
apex_authorization.enable_dynamic_groups (
p_group_names => l_group_names );
END p_post_processing;
29. Click Apply Changes
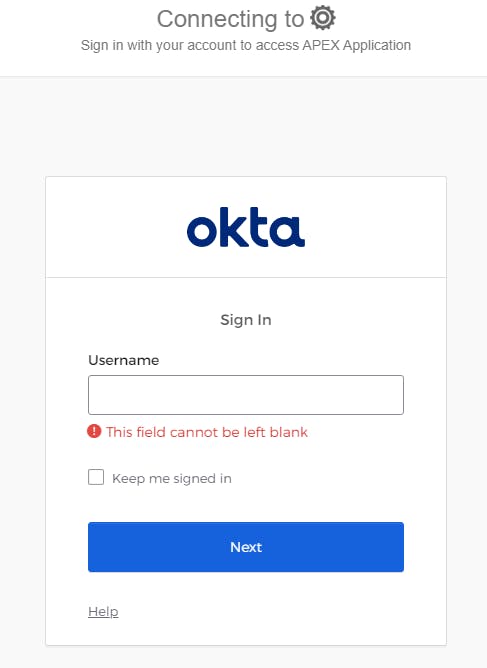
30. Paste the Post Logout URL into a browser Tab (i.e. the one that ends with APEX_AUTHENTICATION=DOMAIN3 )
OKTA login page will be displayed.
31. Enter your password and click Verify
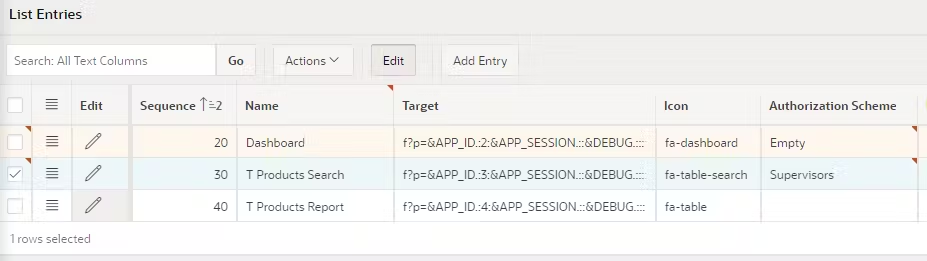
32. Remember when you assigned the Supervisor Role to the Navigation menu?
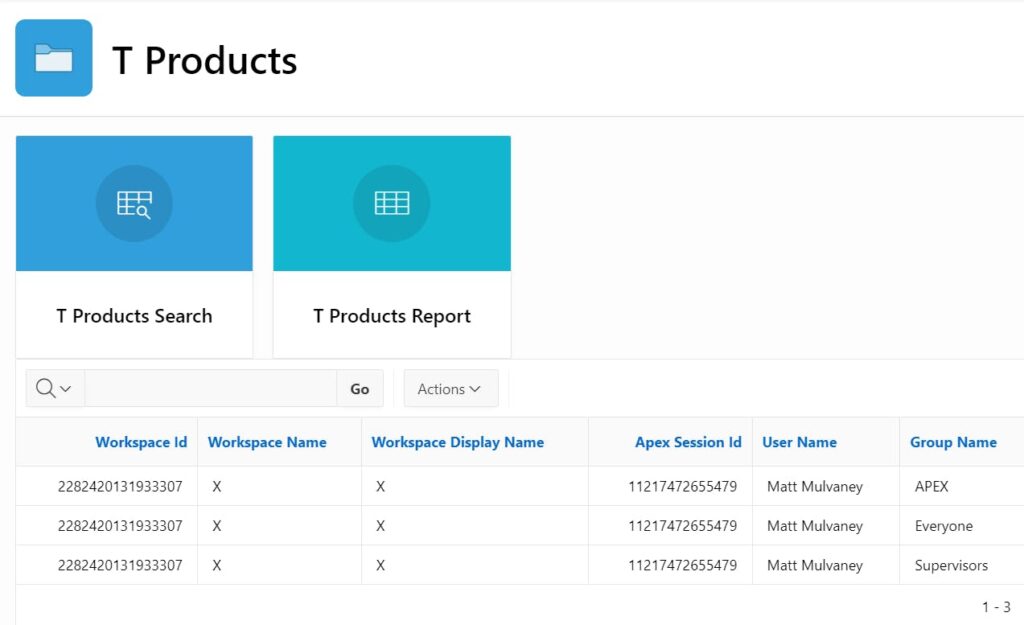
Well, notice that the Supervisor Role has been assigned to the T Products Search card, and the Interactive Report is now showing the correct roles.
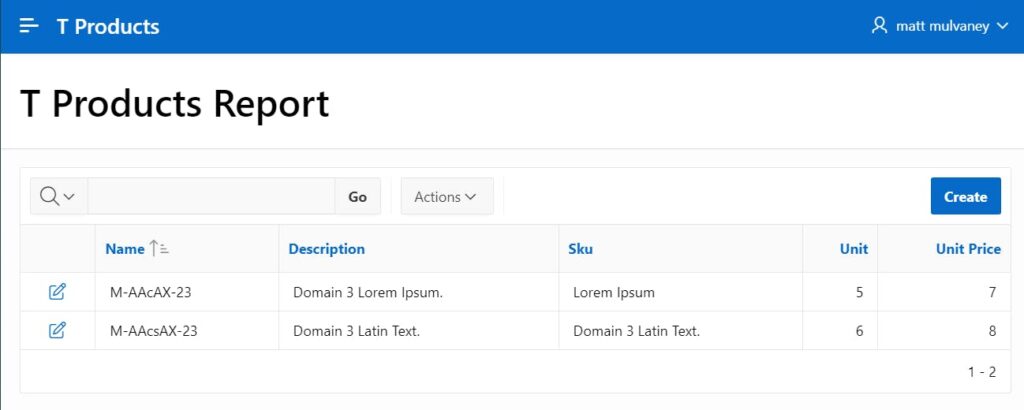
33. Click on T Product Report and notice that the VPD is accurately showing the 2 records associated with DOMAIN3
The username is successfully retrieved.
Conclusion
These are all the steps required to enable OKTA Authentication with APEX. You can use your OKTA Groups and map them to custom roles as needed. I used the following sources while working on this article:
- OKTA authentication for APEX in 5 minutes
- It’s Time for a New Name for APEX Social Sign-In
- What Info is Available from my APEX Social Sign-In Provider?
Also, if you’re interested in APEX-related topics, read my other articles on the Pretius blog. There are quite a few already:
- Oracle APEX Global Notification messages: An easy way to make them look better
- How the Oracle APEX community helps shape the platform’s future
- Oracle APEX new features – the low-code platform keeps evolving
- Oracle 23c Free Docker, APEX & ORDS – all in one simple guide
- Oracle APEX CI/CD: Step-by-step guide aligned to the APEX Application Lifecycle Technical Paper