The single sign-on feature can greatly simplify the authentication in your company applications and help you deal with cybersecurity issues. Keycloak SSO is one of the best options. In this article, we will explain why.
Disclaimer: The original article was published in February 2023, but in October 2023 we updated it with more content, including a chapter on infrastructure and cost estimations, and a free Keycloak Cost Estimation Cheat Sheet. In April 2024, we also added a whole new chapter on the initial setup for Keycloak and a free Keycloak Valuation Form. Finally, a year later – in April 2025 – we’ve updated it with a new section about Keycloak use cases.
What is SSO and why is it worth using?
Single Sign-On (SSO) is a feature that allows your employees to authenticate their identity once within a given system instead of doing it every time they access a different company application. It also lets you simplify your apps – there’s no need to create a login page and authentication mechanism for every app, and you don’t need to deal with user storage. With SSO, users authenticate themselves through a centralized identity provider (IdP) to access multiple applications seamlessly, enhancing both user convenience and security.
In this article, we’ll show you how to enable SSO in your apps using Keycloak – one of the most well-known and secure authorization services which we’ve used in several projects developed for our clients.
What is Keycloak?
Keycloak is a Java-based, open-source Identity and Access Management tool developed by an American software company called Red Hat – the one you may know for its contributions to GNOME and many other open-source projects. It allows you to authenticate and authorize users in your applications securely.
How does it work? It’s pretty simple. Instead of logging into every single application, users do it once on the Keycloak authentication page. After they provide valid identification data (username and password), the technology verifies their identity. It creates a one-time verification code that gets extracted by the app and exchanged for an ID, access and refresh token. Based on that, the system either grants or denies the user access.
Keycloak – main advantages
Here are some of the biggest benefits offered by Keycloak.
Great SSO without a costly investment in custom software
Keycloak allows you to get a great quality SSO system without creating custom software solutions (which can be very costly and time-consuming). Moreover, you don’t have to pay licensing and maintenance fees.
Main business benefit: you save substantial time and money.
Easy setup and integration
Keycloak is incredibly easy to set up and integrate with your apps, requiring little to no coding skills. What’s more, you have plenty of deployment options. You can use Keycloak on-premise or choose a cloud service provider such as Azure Kubernetes. It all depends on your particular needs.
On the front end, you can use customizable, pre-made elements such as screens for user processes (password change, log-in, etc.) and GUIs (graphical user interfaces). Forms and libraries allow you to manage the security flow.
The back end is also pretty easy to take care of. You can use a handy REST API to connect Keycloak to your systems and handle token refreshes, etc.
You can set up a complete logging mechanism using popular social networks, SAML 2.0 Identity Providers (IdP), an existing OpenID Connect, or LDAP / Active Directory servers.
Main business benefit: fast integration means faster app implementation in your company. You also have the flexibility to integrate with your existing systems, so there’s no need for additional costly development.
Top-of-the-line security
No issue’s more important for an access control system than security – it could be argued that’s the whole point of its existence.
The common sense approach is to use solutions that other companies have tried and tested. After all, it’s certainly better to learn from someone’s example than be a source of such a lesson for others. Keycloak is one of the best and, therefore, the most tested and well-known options on the market.
Main business benefit: top-of-the-line security tested by many other organizations. In fact, most of your security needs can be covered just with Keycloak.
A powerful feature set
Here are some of the features offered by Keycloak:
- Roles and subgroups – Keycloak allows you to assign users to individual roles and subgroups. You can also assign them specific components – such as GUI elements or API functions. This lets you limit the access of certain people and positions to parts of the application to reflect company structure and the division of responsibilities.
- Central administration management – you can manage the administration centrally via Keycloak Admin Console and Account Management Console. The first allows you to manage users’ permissions and sessions and limit access to features. The second one lets users modify their own accounts.
- Impersonation – it allows certain users – such as members of the customer support team – to “impersonate” someone to retrace their steps and help them with their problems.
- Advanced password policy – you can decide how complex the passwords in your organization are to be. Keycloak allows you to set minimum length, require people to use lowercase, uppercase, and special characters, or limit their ability to do so. It’s up to you and the security standards in your company.
- Plugin-based architecture – adding new functionalities to Keycloak is often as easy as installing a plugin. You don’t have to change elements of the entire system through development, which means you save money.
Main business benefit: great adaptability and scalability. You get a modern, feature-rich access management system that scales with your business as it grows. You can also further expand the solution’s functionality depending on your needs, and it doesn’t require a big investment.
Ongoing development
Despite its age (the first release was in September 2014), Keycloak is still an evolving technology. New versions get published periodically – the last stable build showed up on GitHub in March 2025, just a few weeks ago. What this means is that the tool still gets new features and enhancements.
There’s also a pretty big and active community around Keycloak. The developers who form it create great plugins and are always ready to answer burning questions. If you need help with something, you can simply ask (on the aforementioned GitHub page, for example, but there are also many Keycloak-related threads on Stack Overflow).
Main business benefit: despite many years on the market, Keycloak is not legacy technology. You have access to updates and a thriving community.
Keycloak – common use cases
Here are several typical use cases for the Keycloak IAM technology:
Improving security
Keycloak offers a range of authentication methods, such as username/password and multi-factor authentication. You can also integrate it with external identity providers. Depending on the selected tool, the system allows you to monitor user authentication activities and create audit logs. The solution is fully compliant with regulations such as GDPR, HIPAA, and PCI DSS.
Centralizing user management
Keycloak lets you integrate user identities from different sources, helping organizations manage users across various domains and realms. Furthermore, it enables companies to establish detailed access control policies based on attributes, roles and permissions. Thanks to this, you can ensure users have the correct level of access to resources.
Enhancing UX
With SSO, users can log into multiple applications using just one set of credentials, removing the hassle of managing multiple logins. Keycloak also includes features for user self-registration, password resets, and profile management – everything necessary to set up and manage your account.
Migrating from a different IAM technology
Occasionally, companies already use an IAM system but seek to switch to an open-source option (such as Keycloak). This can be motivated by dissatisfaction with the existing software, a desire to evade high licensing fees of a commercial product (particularly problematic if your company grows rapidly) or a necessity to transition from a legacy system.
Learn from our experience – a Pretius project with the Keycloak authentication system
We’ve used Keycloak during a project for a large European construction business, for which we’ve created several systems – self-care, administrative, and various microservices – used both by the company’s employees and partners from outside (contractors).
We’ve decided on Keycloak for several reasons:
- It uses OpenID Connect, which is a well-known standard
- It’s open-source and free, unlike some of the competition (like Okta)
- It’s well-known and battle-tested, and there aren’t, in fact, that many solutions like that (we’ve considered Keycloak, Okta, and CAS, but we’ve had previous experience with that last solution, and we decided we want something different)
- There are many examples of successful front-end and back-end integrations. Keycloak has a dedicated JavaScript library, and you can use universal libraries for Java
- It’s easy to customize thanks to Java-based extensions
- There are many ready-made extensions on the Internet
- It fulfilled many of our project requirements out of the box
- It has an administrative panel by default
- Keycloak has a well-documented administrative API which you can use, for example, to manage users from microservices
Our Keycloak implementation works like this: we’ve built a Keycloak’s Docker image, which runs on Kubernetes. Keycloak’s public API is visible to “the world” (i.e., all users who know of the system), whereas the administrative API is hidden and available only in the interior network.
We’ve had to write several custom extensions and implemented Configuration as Code (CaC). Thanks to this, the configuration changes are implemented automatically – administrators don’t have to make them in every environment. We’ve used the keycloak-config-cli tool, which is available on GitHub.
The end result? Users of the company’s multiple systems and microservices can now log in using the Keycloak SSO system.
How to set up and configure Keycloak
Disclaimer: The settings presented here should never be used in a real application. Our aim was to show you the basic configuration options and illustrate the solution’s ease of use. Because of that we have made numerous simplifications (such as using “admin” as the default password to the admin panel, etc.). If you want to configure Keycloak to work with a complex and important system, we encourage you to read the official documentation or contact us at hello@pretius.com – we’ll be happy to help you with your Keycloak project.
First, download the Keycloak image for Docker from the official website and run it in your local environment. You can do this quickly using the following command in your CLI:
Here are a couple of tips from our talented devs that should help you implement Keycloak and configure single sign-on in your project without too many problems:
docker run -p 8080:8080 -e KEYCLOAK_ADMIN=admin -e KEYCLOAK_ADMIN_PASSWORD=admin quay.io/keycloak/keycloak:23.0.4 start-dev
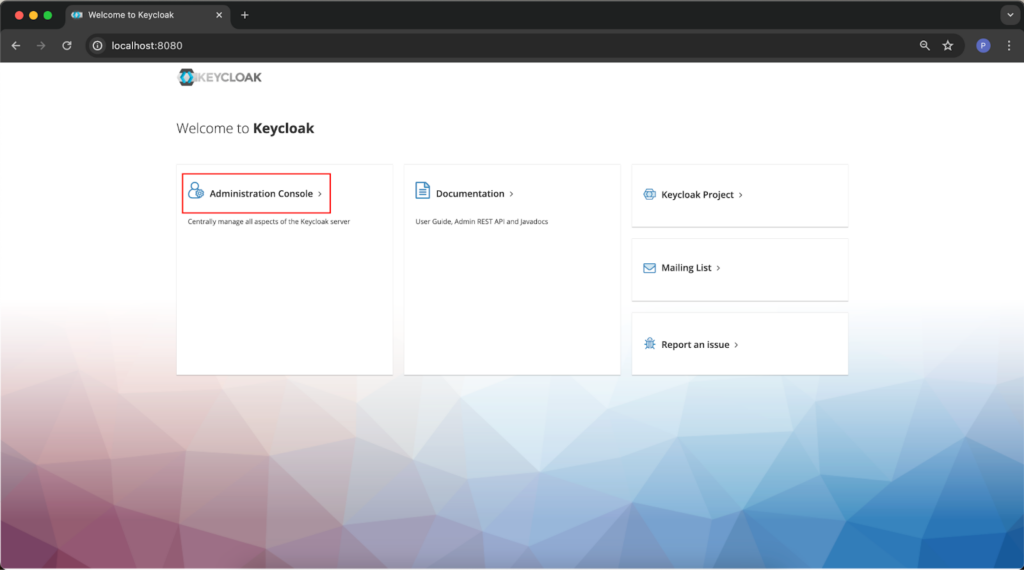
The next step is to configure Keycloak. Go to http://localhost:8080, where you will see the Keycloak welcome page. It contains links that allow you to perform basic operations. Click on the one that opens the administration console (the area marked in red on the screenshot below).
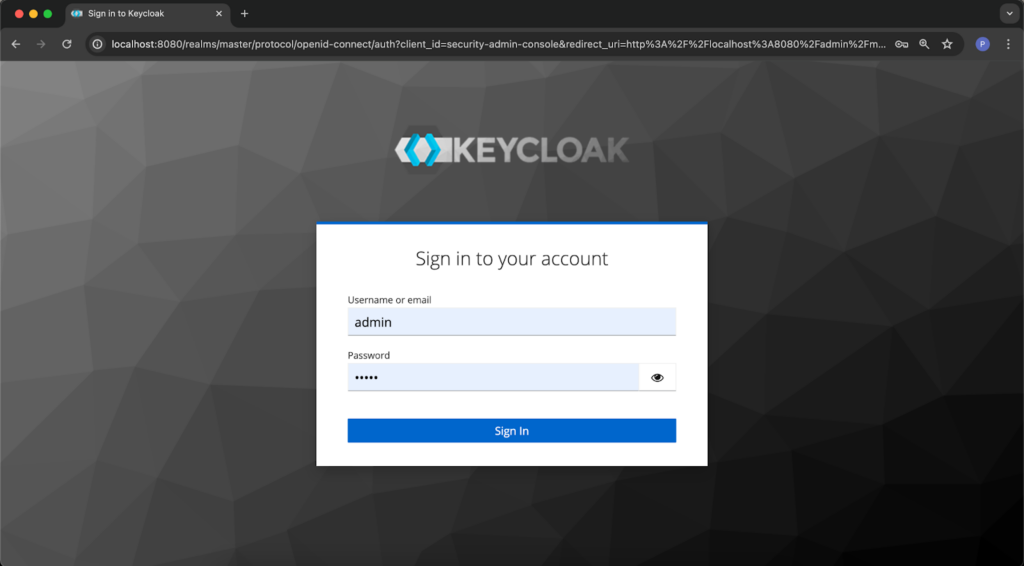
Enter the default login and password for the administrator account here. If you used the CLI command given at the beginning, enter “admin” in both fields.
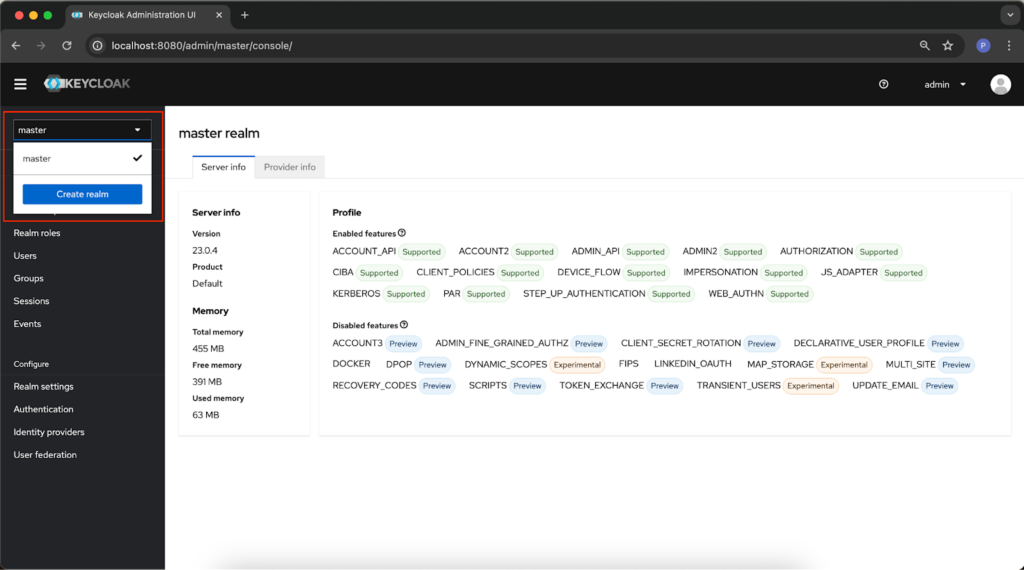
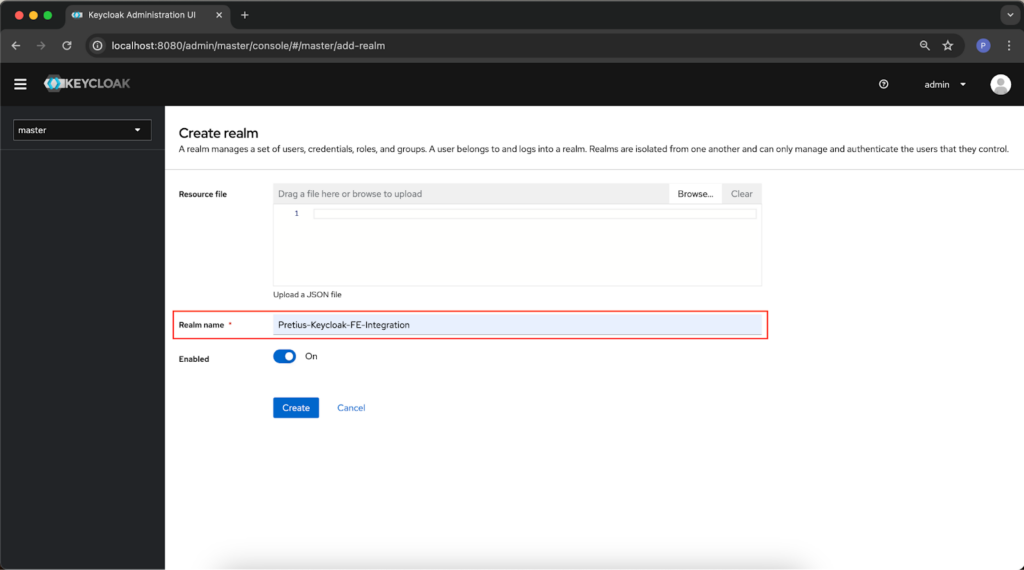
The next step is to create a new realm. To do this, click on the field in the upper left corner of the application (it will probably be called “master”) and click Create realm.
For the purpose of our article, we named our realm “Pretius-Keycloak-FE-Integration”, but the name isn’t important – you can choose any.
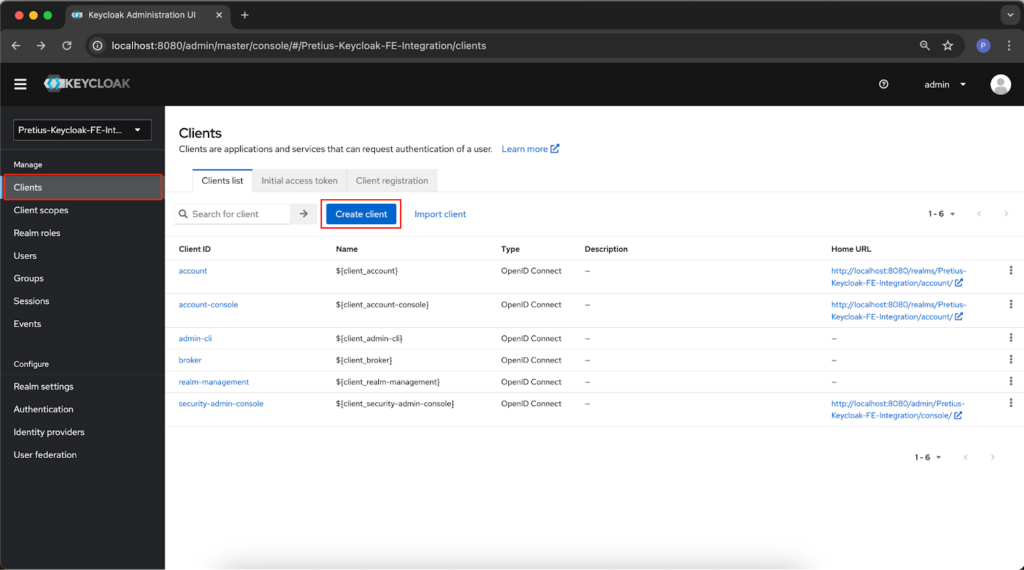
After creating a new realm, configure it using the settings available in Realm Settings. You don’t have to make changes, but adding a new client is important, which will be the app you want to use Keyloak with. Go to the Clients tab and select Create client.
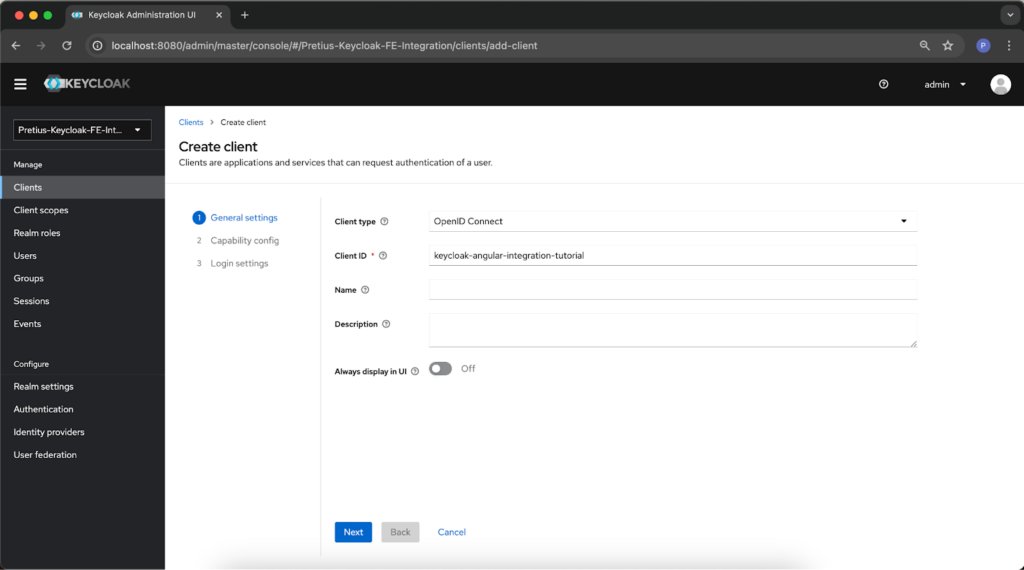
Then, specify the Client type (we left the default one) and the Client ID. You can also add a name and/or description and make the client to be always displayed in the UI.
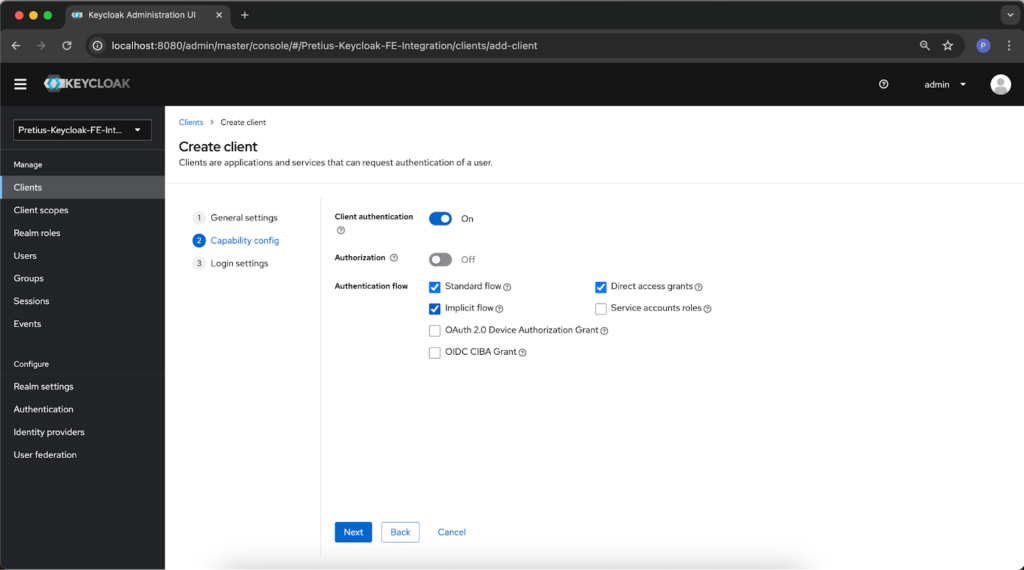
The Compatibility config tab allows you to toggle client authentication and authorization and define the authentication flow. We’ve used these settings for demonstration purposes:
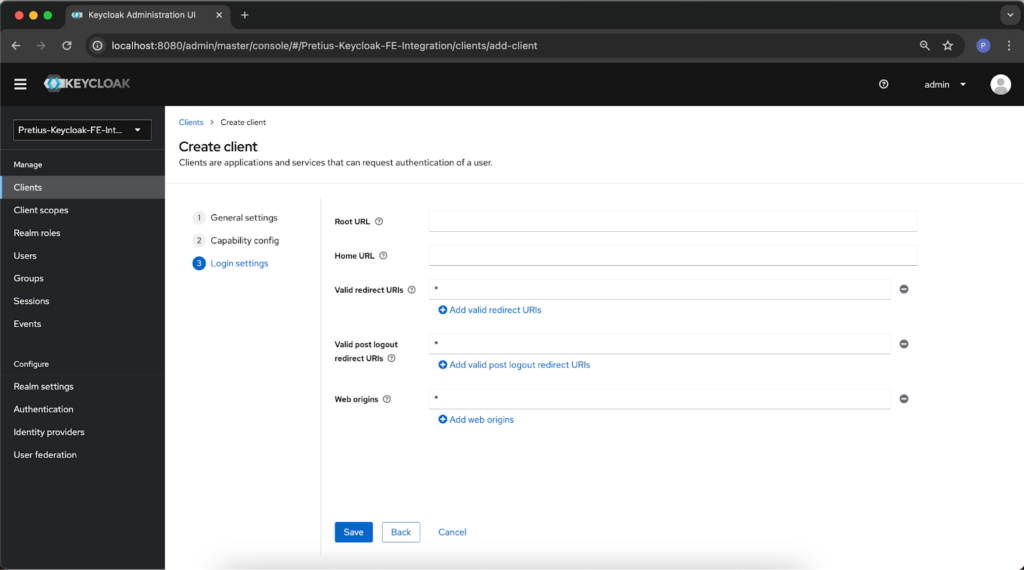
You can also change some Login settings. In these fields, you can provide valid redirect URIs that will be allowed when users are redirected after logging out. We placed asterisks there for a reason – they can replace any string of characters, so it’s possible to redirect literally anywhere. Of course, this isn’t necessarily what you want to allow – so specify the URLs according to your needs, and click the Save button to save your changes.
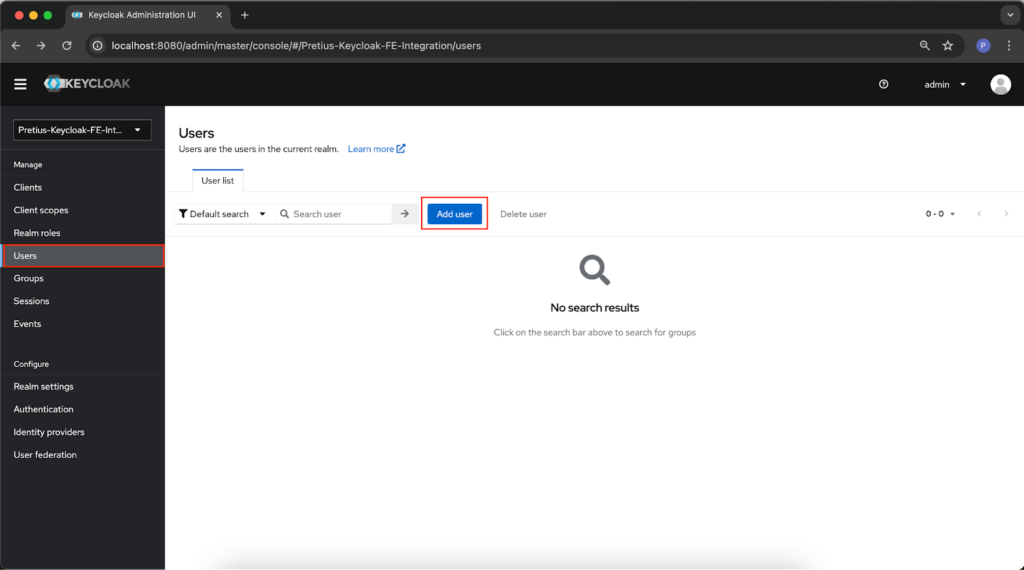
All that’s left to do is to create a user that will allow you to log in to Keycloak from the application. Go to the Users tab and click Add user
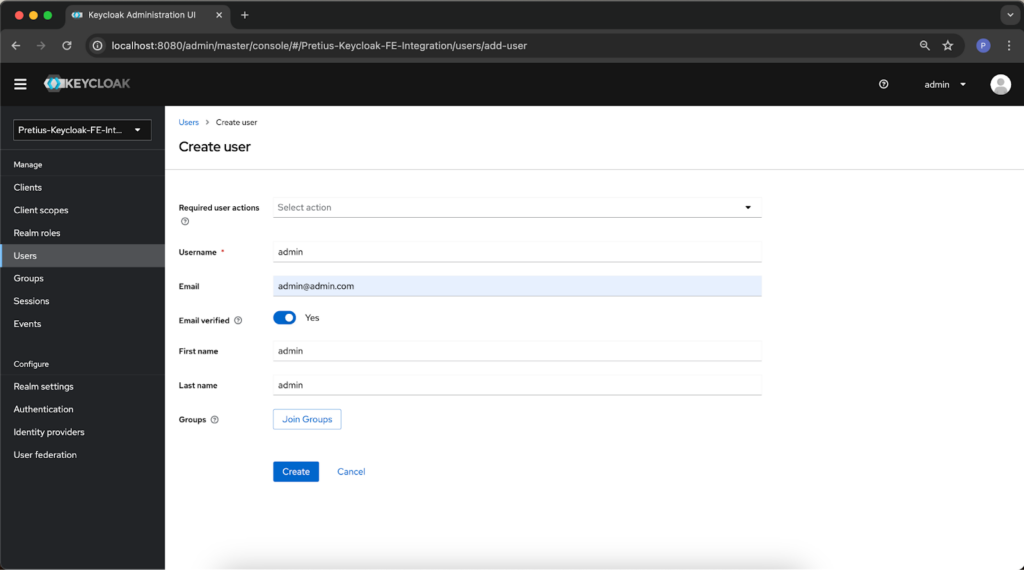
Fill out the user information in any way that suits you, for example:
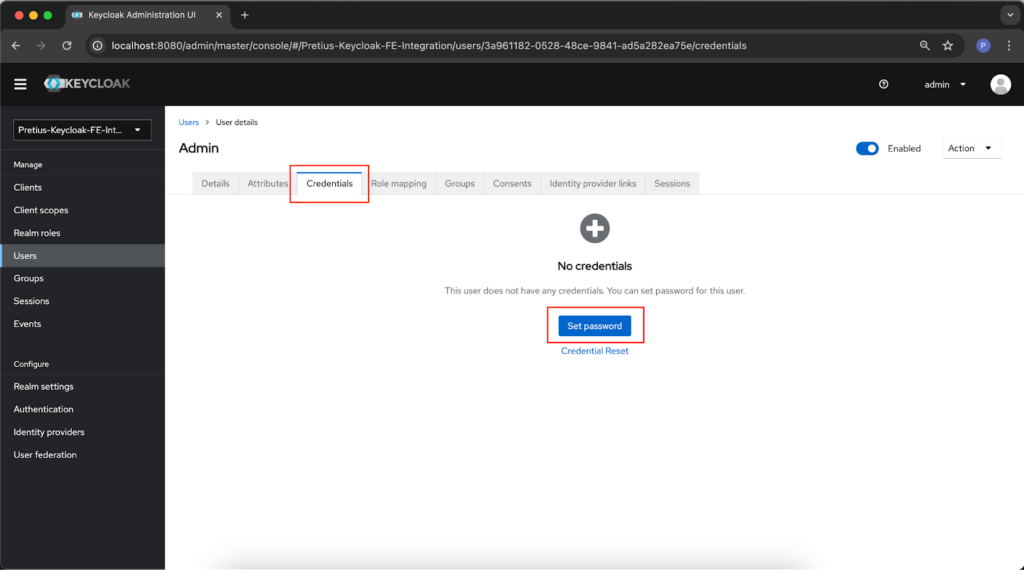
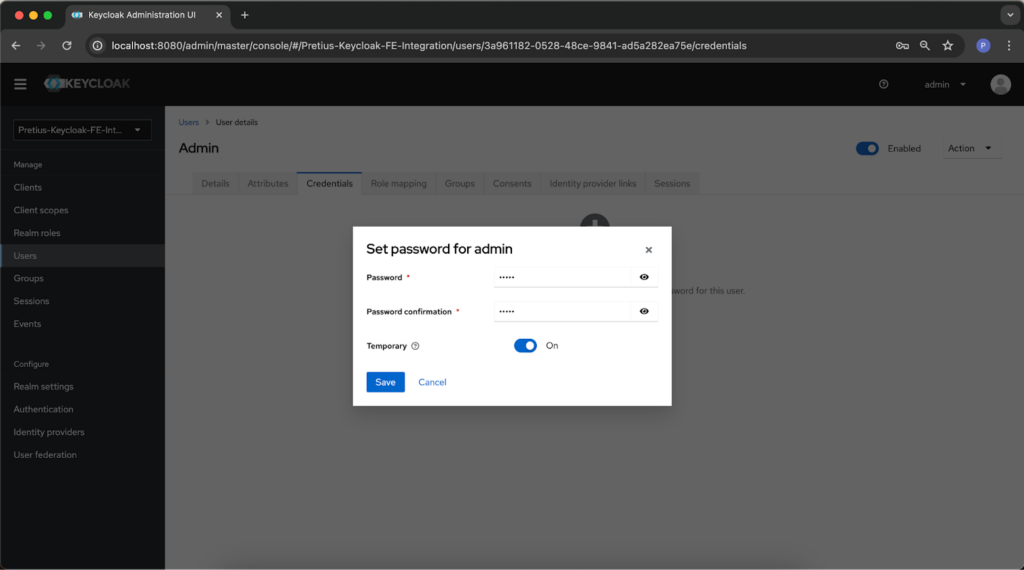
Confirm the data by pressing the Create button. It’s also necessary to give the user a new password in the Credentials tab – press the Set password button.
And that’s about it – the initial setup is done. After you integrate your application with Keycloak (we won’t cover this step here as the particulars can differ, but we’ve described a sample Keycloak-Angular integration in a separate article), you can use your created user to authenticate via Keycloak.
Helpful tips from our Developers
Here are also a couple of advanced tips from our talented devs that should help you implement Keycloak and configure single sign-on in your project without too many problems:
- Get to know the authorisation and authentication standards (OAuth, OpenID Connect)
- Be sceptical about the idea of extending the solution. Adapt to existing functions first and extend only if necessary. This component is responsible for authentication and authorization, so there is no room for error here
- When implementing Identity Access Management on your own, you must ensure HA, scaling, backups, etc.
- Choose the “owner” of the solution. This is a very specific component in the ecosystem and, in our experience, it’s not always evident who’s responsible for it
- Before you start with the implementation, you need to establish standards for using IAM in the organization, processes for assigning/reporting permissions, and policies regarding the quality of passwords (length, characters, expiration time, etc.)
- In the case of an external identity provider (e.g., the organisation’s Active Directory), you also need to prepare appropriate permissions for Keycloak, network copies to AD and define the scope of data downloaded from the source system. Integrating systems must confirm the ability to authenticate users on the front end (standard OIDC mode), and back-end systems must confirm the ability to authenticate in the “client credentials” mode. Each system accepting certified queries must be able to verify the correctness of these credentials (in the case of a JSON Web Token – the validity and token signature, claims with permissions)
Infrastructure and cost estimation
We’d also like to provide you with a cost estimation for a Keycloak implementation project. Our estimates use the example of the cloud infrastructure based on Microsoft Azure technology. However, the costs for other cloud platforms (e.g., AWS) are very similar.
Main project assumptions
- We want the possibility to use Keycloak as an independent Identity Provider
- We’re using using Keycloak mainly for SSO and MFA (TOTP)
- The API available within Keycloak is not used in this example, as it is needed only in specific business scenarios (e.g., for instance when you want to integrate with some other services, e.g. external user management service)
- We’re deploying to the Azure cloud and want to ensure the solution’s self-sufficiency
- The target costs of implementing and maintaining infrastructure may vary, depending on the individual needs of the organization, including the number of maintained users, the amount of data processed, the region, the need to ensure high availability, as well as whether the organization has cloud competences or whether it is necessary to provide support from external specialists
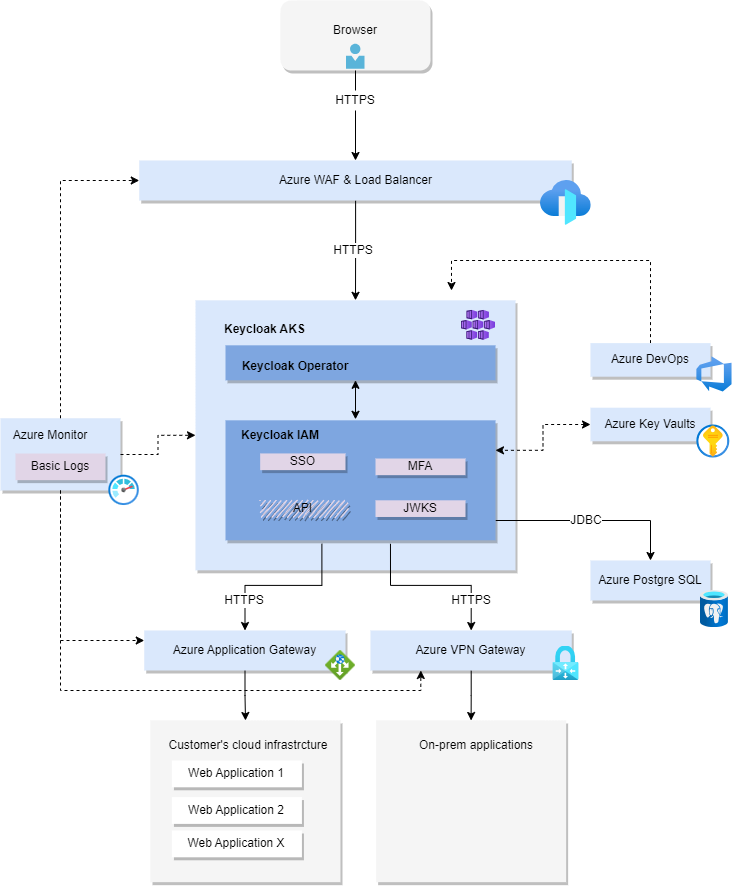
Example infrastructure
Our example infrastructure assumes a connection to both the organization’s web applications and on-premise applications. Of course, the parameters, as well as cloud resources and services, are only estimates. Ultimately, the costs will differ for each organization, depending on its needs and specifics (for example, using a different type of database).
Infrastructure assets and elements
- Azure Kubernetes Service (AKS) – Managed Kubernetes service, container orchestration
- Azure Front Door – load balancer and WAF (Web Application Firewall)
- Azure PostgreSQL – database for Keycloak applications
- Azure VPN Gateway – connection to the local network
- Azure Application Gateway – connection to other cloud services
- Azure Monitor – monitoring and logs
- Azure Key Vault – safe storage and access to secrets, e.g. verification certificate
- Azure DevOps – implementation and version management
The final cost
So, how much do all of these elements cost? It depends on the environment (production or dev/test) and your chosen subscription. For example, with the “pay as you go” pricing model, the estimated cost is around $625,63/month. However, you can lower it substantially by choosing a 1-year or 3-year reservation.
If you want to check all the details, we’ve created the Keycloak Cost Estimation Cheat Sheet – an easy-to-use PDF file to help you estimate the cost in your company’s case. We use it on a daily basis at Pretius when estimating the IAM/SSO projects for our clients. You can download the cheat sheet for free by using the form below.
There are also additional factors that may affect the cost of maintaining the platform:
- Sometimes, it’s possible to use the organization’s existing infrastructure, which may reduce the costs
- Each organization may have different needs and requirements regarding factors affecting performance, i.e. the number of users and applications used
- If licenses for Microsoft products (database, operating system, etc.) are available within the organization, they can be used within the Azure cloud infrastructure
- Depending on business needs, additional resources other than those listed above may be required (for example, Microsoft Azure Manged Disks resources)
- If the organization lacks cloud competencies, the costs of hiring a specialist or renting a service providing appropriate support should also be taken into account
- The selected type of support provided by Microsoft Azure can also affect the cost
Summary: Consider Keycloak as your access management solution
Keycloak is a great IAM option. It helps you optimize costs, keep time to market in check, and provides top-notch security based on a tried-and-tested solution. The tool is also adaptable (especially when you already have Java in your tech stack), scalable, and constantly updated with new features. You seriously can’t go wrong with it, and in many cases, it’s a much better choice than going for a costly custom software development.
Do you need any help with a Keycloak implementation? Or maybe you don’t know how to configure the single sign-on properly? Reach out to us at hello@pretius.com or use the contact form below. We have a great deal of experience with creating custom IAM solutions based on Keycloak, and we can show you a practical demo of an application integrated with the Keycloak system during free consultations. Expect our answer within 48 hours.
If you’re interested in cooperating with us, you can also download and fill out our Keycloak Valuation Form – it’ll help you prepare for implementing Keycloak and help us better understand the scope and goals of your project.
Keycloak SSO – FAQ
Here are some frequently asked questions regarding Keycloak Single Sign-On.
What is Keycloak?
Keycloak is an open-source software solution that provides single sign-on access to applications and services. It allows users to authenticate once and access multiple applications without re-entering their credentials.
What’s the newest version of Keycloak?
At the time of writing this article, the newest version of Keycloak is 26.1.4, released in March 2025.
What are the best Keycloak features?
The platform offers many useful features, including roles and subgroups, central administration management, impersonation, advanced password policies, and plugins.
How to use Keycloak?
Keycloak is easy to set up and use and you can deploy it on-premise or use a cloud platform (AWS, Azure, etc.), which enables cloud identity and access management. You can integrate with existing applications and systems. Keycloak provides a secure way of authenticating users and allows them to access various resources and services with a single set of credentials.
How Keycloak works?
Keycloak stores and manages user information, permissions, and other configuration data, as well as information regarding the authentication methods used for each application. The solution supports a range of authentication protocols, including OpenID Connect, SAML, and OAuth2.
Once a user logs in to the Keycloak server, they are authenticated, and their identity is verified. The user’s identity is then mapped to the applications they can access. Keycloak’s authorization system allows administrators to define what apps particular users can access and what they can do within those systems.